思路
配置
configure terminal access-list 701 permit 0026.5a0e.3123 0000.0000.0000 dot11 association mac-list 701
configure terminal access-list 701 deny 0026.5a0e.3123 0000.0000.0000 dot11 association mac-list 701
范例
ap#show dot11 associations
802.11 Client Stations on Dot11Radio0:
SSID [CORPORATE] :
MAC Address IP address Device Name Parent State
0026.5a0e.3123 10.100.146.129 ccx-client – self Assoc // JUST ALLOW THIS
10a5.d0e0.7456 10.100.146.133 ccx-client – self Assoc
ap#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
ap(config)#access-list ?
<1-99> IP standard access list
<100-199> IP extended access list
<1100-1199> Extended 48-bit MAC address access list
<1300-1999> IP standard access list (expanded range)
<200-299> Protocol type-code access list
<2000-2699> IP extended access list (expanded range)
<700-799> 48-bit MAC address access list
dynamic-extended Extend the dynamic ACL absolute timer
rate-limit Simple rate-limit specific access list
ap(config)#access-list 701 ?
deny Specify packets to reject
permit Specify packets to forward
ap(config)#access-list 701 permit ?
H.H.H 48-bit hardware address
ap(config)#access-list 701 permit 0026.5a0e.3123 ?
H.H.H 48-bit hardware address mask
<cr>
ap(config)#access-list 701 permit 0026.5a0e.3123 0000.0000.0000
ap(config)#
ap(config)#dot11 association ?
mac-list filter client with a MAC address access list
ap(config)#dot11 association mac-list ?
<700-799> Ethernet address access list
ap(config)#dot11 association mac-list 701 // APPLY TO RADIO INTERFACE
ap(config)#
*Oct 28 09:49:01.194: %DOT11-6-DISASSOC: Interface Dot11Radio0, Deauthenticating Station 10a5.d0e0.7456
*Oct 28 09:49:01.194: %DOT11-6-DISASSOC: Interface Dot11Radio0, Deauthenticating Station d025.988f.7789
*Oct 28 09:49:01.374: %LINK-5-CHANGED: Interface Dot11Radio0, changed state to reset
*Oct 28 09:49:01.403: %LINK-3-UPDOWN: Interface Dot11Radio0, changed state to up
*Oct 28 09:49:01.414: %DOT11-4-MAXRETRIES: Packet to client 10a5.d0e0.7456 reached max retries, removing the client
*Oct 28 10:12:04.141: %DOT11-6-ASSOC: Interface Dot11Radio0, Station 0026.5a0e.3123 Associated KEY_MGMT[NONE]
ap#show dot11 associations
802.11 Client Stations on Dot11Radio0:
SSID [CORPORATE] :
MAC Address IP address Device Name Parent State
0026.5a0e.3123 10.100.146.129 ccx-client – self Assoc
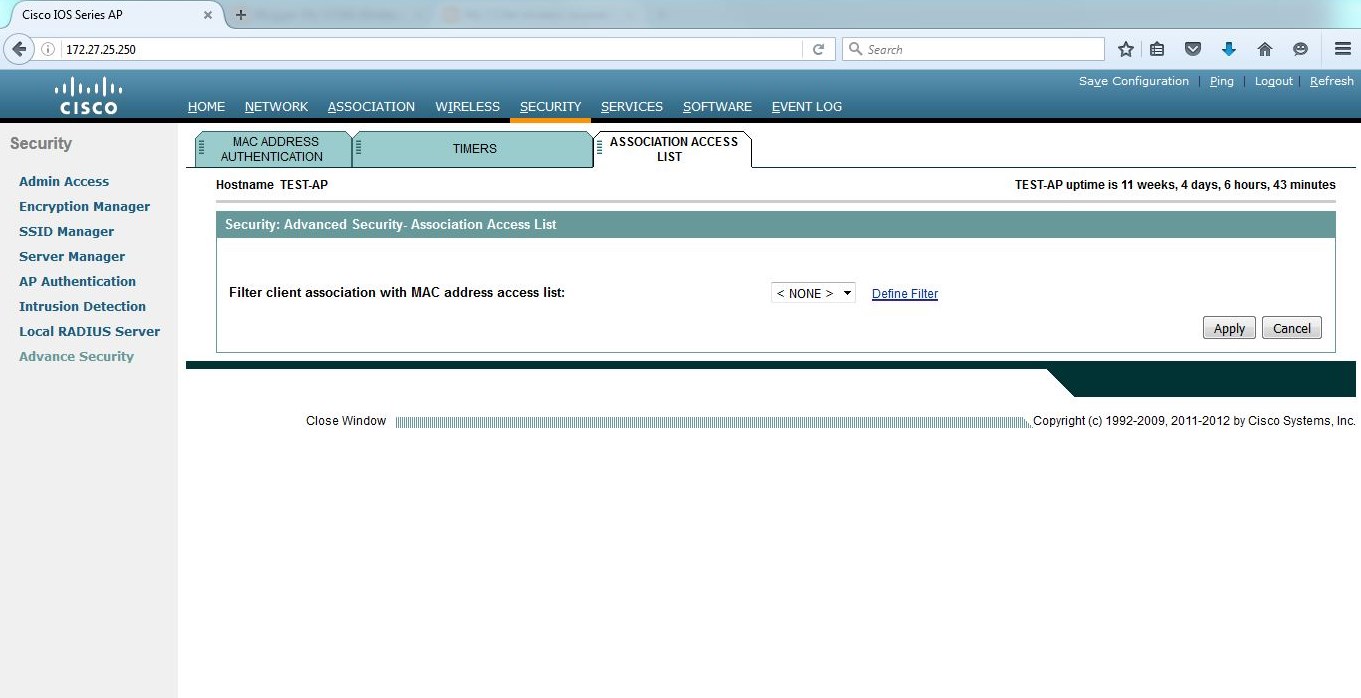
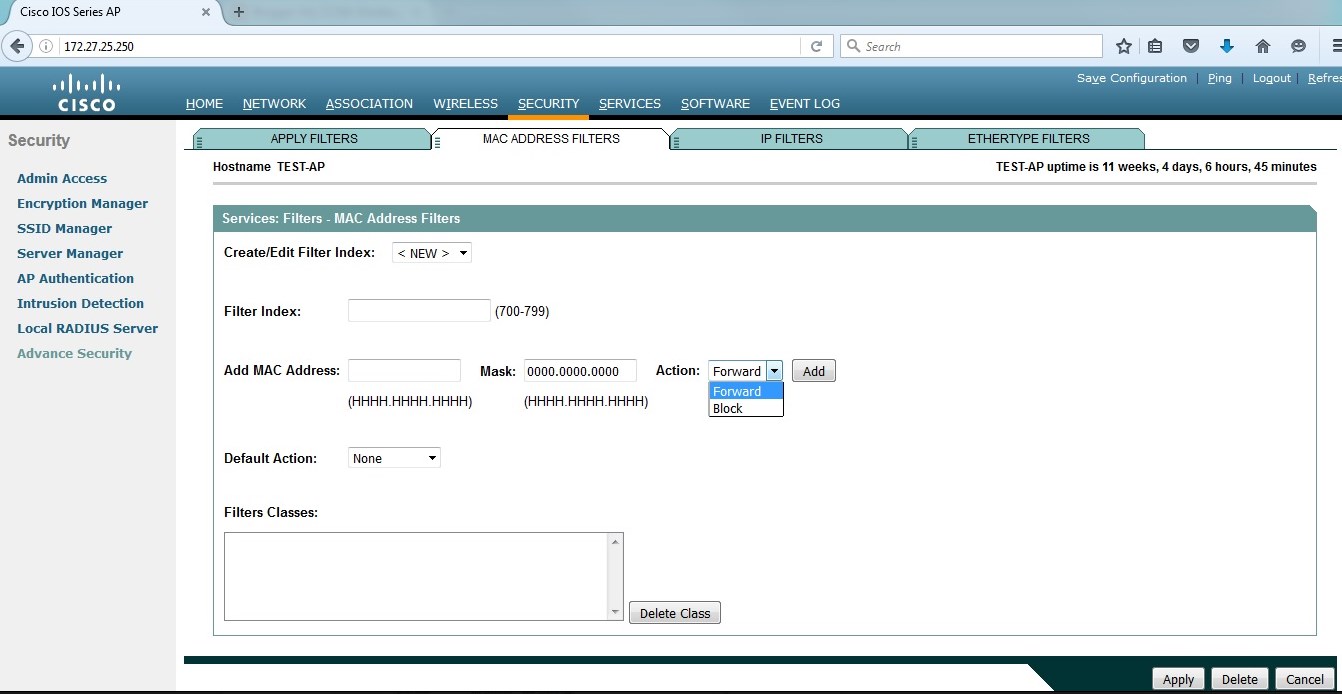
附:web配置方法